The SDP2 solves all 19 data storage and data management related control requirements out of the box.
DFARS compliance is mandatory for all DoD contractors by December 31, 2017. DFARS clause 252.204-7008 addresses requirements for safeguarding covered defense information controls in government contractor systems. Covered defense information is a broad term for Controlled Unclassified Information (CUI), which has protection and dissemination requirements. This kind of data is common among DoD contractors and this requirement applies to all contractors regardless of their size. These mandatory controls are detailed in the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171: Protecting Controlled Unclassified Information in Non-Federal Information Systems and Organizations.
There are 109 controls in the NIST Special Publication and 19 of them pertain to data storage, data management, data sanitization, encryption, key management, access control, and audit accountability. The SDP2 platform delivers high performance shared storage with FIPS 140-2 Certified key orchestration and data encryption. SDP2 is a drop in solution you can use to host any virtualized infrastructure, application or file shares without a change to your current workflow. For a detailed list of controls, and to see how SDP2 satisfies the control, review the list below.
The 19 Controls SDP2 Addresses Out of the Box
- Control 3.1.1 Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- BrickStor’s Microsoft Active Directory integration and security groups enables compliance with ease. Admins just need to maintain appropriate users in each security group.
- Control 3.1.7 Prevent non-privileged users from executing privileged functions and audit the execution of such functions.
- SDP2 provides role based access controls and a full audit of activities on the system by admins and users.
- Control 3.1.21 Limit use of organizational portable storage devices on external information systems.
- SDP2 offers an easy method providing authorized access to data from a central protected location. SDP2 can be used for VDI as well as a file sync and share repository negating the need for users to use portable storage devices such as USB drives.
- Control 3.3.1 Create, protect, and retain information system audit records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful, unauthorized, or inappropriate information system activity.
- The solution provides full audit log of everything that can be retained on the system and or sent to a log repository and System Issue Event Manager (SIEM).
- Control 3.3.2 Ensure that the actions of individual information system users can be uniquely traced to those users so they can be held accountable for their actions.
- Granular auditing on a per user and per transaction basis provides full accountability and can be used for forensic investigations and prosecution.
- Control 3.3.7 Provides an information system capability that compares and synchronizes internal system clocks with an authoritative source to generate time stamps for audit records.
- SDP2 maintains timing synchronization with network time protocol (NTP) ensuring logs use the correct time stamp.
- Control 3.3.8 Protect audit information and audit tools from unauthorized access, modification, and deletion.
- Logs on the system can be replicated automatically and immutable snapshots are taken of logs to prevent tampering. Logs can also be sent to a SIEM.
- Control 3.4.1 Establish and maintain baseline configurations and inventories of organizational information systems (including hardware, software, firmware, and documentation) throughout the respective system development life cycles.
- BrickStor maintains serial number and firmware version for all components in a database and can ensure original authentic parts through a secure supply chain.
- Control 3.7.3 Ensure equipment removed for off-site maintenance is sanitized of any CUI.
- All SDP2 drives are FIPS certified self encrypting drives that are capable of cryptographic erasure for media sanitization compliant with NIST SP 800-88 Revision 1.
- Control 3.8.1 Protect (i.e., physically control and securely store) information system media containing CUI, both paper and digital.
- SDP2 protects all data at rest and replicated data in transit with encryption. All drives use inline AES-256 encryption with zero impact to performance.
- Control 3.8.2 Limit access to CUI on information system media to authorized users.
- SDP2 has strong access controls and integration with Active Directory to ensure access is limited to authorized users.
- Control 3.8.3 Sanitize or destroy information system media containing CUI before disposal or release for reuse
- All SDP2 drives are Seagate TAA/BAA FIPS certified self encrypting drives that are capable of cryptographic erasure for media sanitization compliant with NIST SP 800-88 Revision 1.
- Control 3.8.6 Implement cryptographic mechanisms to protect the confidentiality of CUI stored on digital media during transport unless otherwise protected by alternative physical safeguards.
- All SDP2 drives are Seagate FIPS 140-2 certified self encrypting drives. All data is encrypted using AES-256. Disks and SSDs can be safely transported.
- Control 3.13.8 Implement cryptographic mechanisms to prevent unauthorized disclosure of CUI during transmission unless otherwise protected by alternative physical safeguards.
- Data replication between SDP2 platforms is always encrypted and protected.
- Control 3.13.10 Establish and manage cryptographic keys for cryptography employed in the information system.
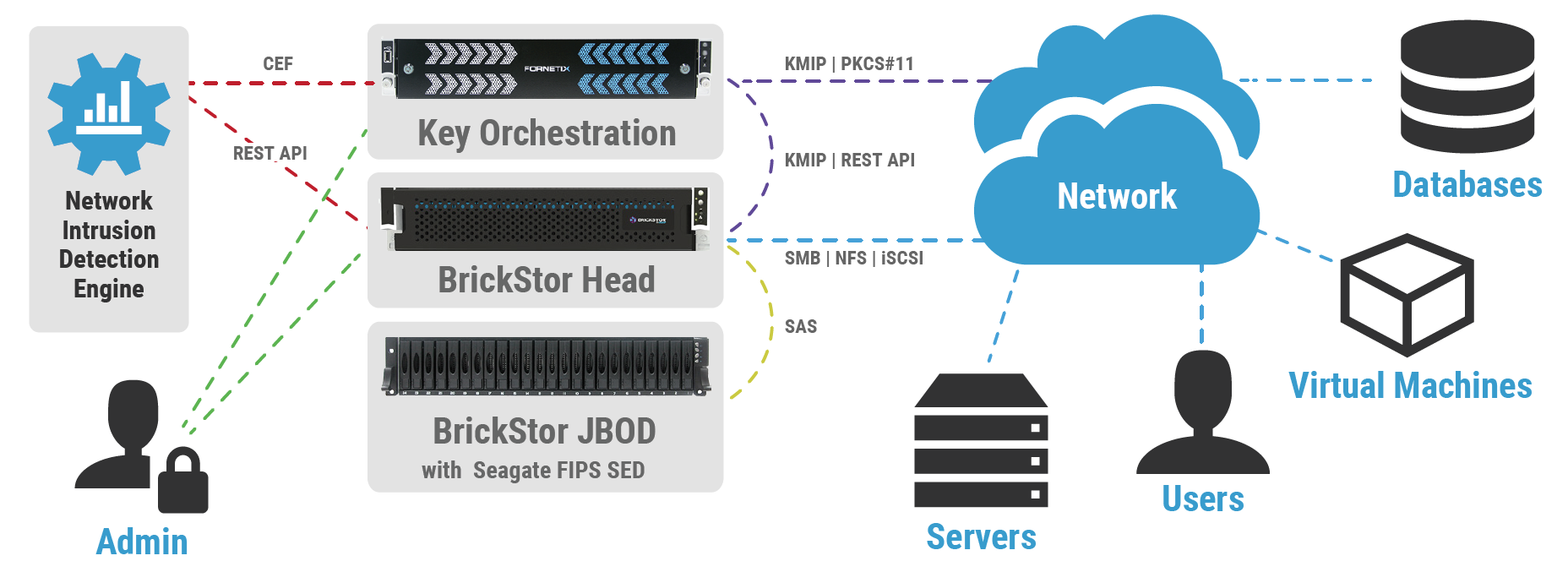
- SDP2 employs Fornetix Key Orchestration to manage, rotate, and life-cycle keys and certificates within SDP2 and other tangential information systems.
- Control 3.13.11 Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.
- The drives and key orchestration appliance within SDP2 are FIPS 140-2 validated.
- Control 3.13.16 Protect the confidentiality of CUI at rest.
- All data is protected at rest through access controls, user permissions and FIPS 140-2 validated encryption.
- Control 3.14.2 Provide protection from malicious code at appropriate locations within organizational information systems.
- BrickStor automatic malware and ransomware protection automatically enables organizations to roll back to a version from a period before issue noticed/surfaced.
- Control 3.14.6 Monitor the information system including inbound and outbound communications traffic, to detect attacks and indicators of potential attacks.
- SDP2 offers the ability to monitor user actions and discover anomalies in the behavior of a user’s or application’s interaction with data.