Active Defense with BrickStor SP
Don't wait to find out what your backups are missing - deploy Cyberstorage for active defense against cyber threats
BrickStor SP: Active Defense
Deploy BrickStor SP to defend your sensitive unstructured data from cyber threats in real time
Traditional file storage systems are a hacker’s paradise, and continue to be exploited by malware infected clients, advanced persistent threats, and malicious insiders. While cyber solutions will protect your perimeter defenses, and passive security or WORM solutions may protect your backups, neither do anything for data in its most vulnerable position – on primary storage systems and online archives in the cloud, at the edge, or in the data center.
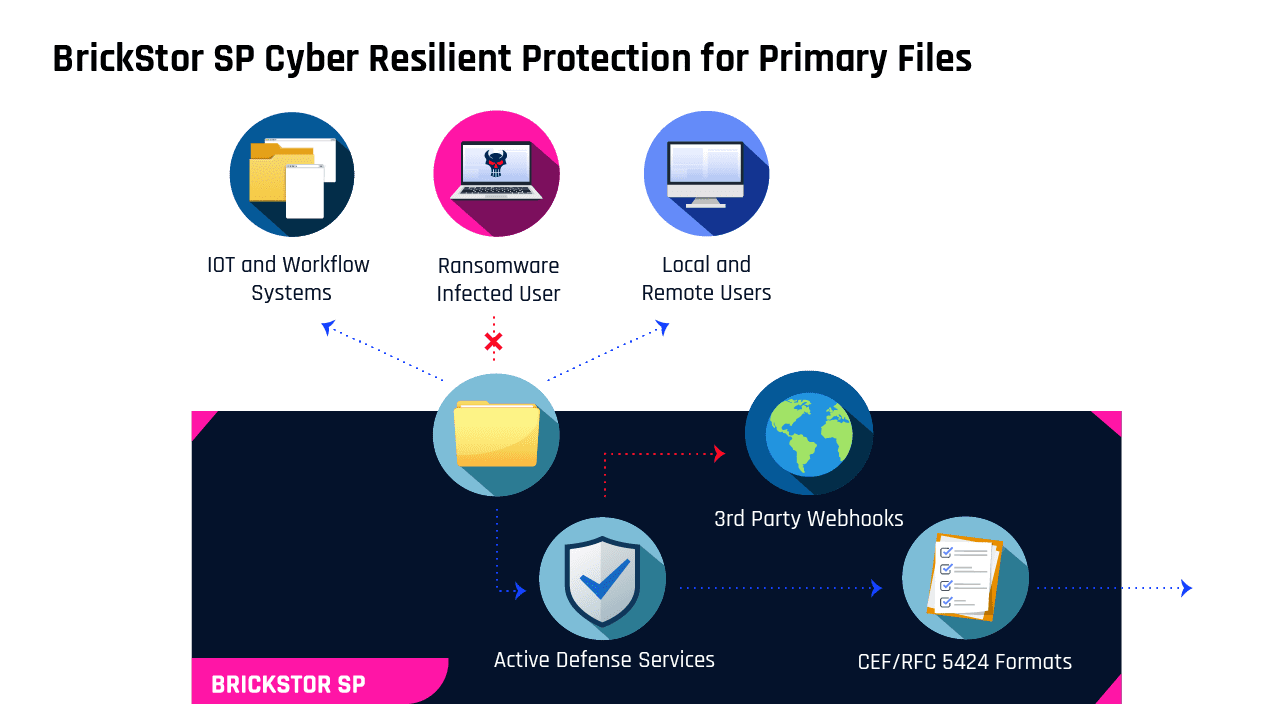
RackTop’s BrickStor Security Platform (SP) is the only software defined primary data storage solution that can defend your files from the most severe cyber threats and take active measures to stop ransomware, data theft and cyber attacks in real time.
Here’s how it works

BrickStor: Active Defense Demo
BrickStor SP active security architecture implements zero trust principles to protect your files. In the same way the credit card industry evaluates each charge transaction, BrickStor SP actively evaluates trust for each file operation in real time based on client IP, user account, file activity and other behavioral identifiers to provide security and visibility necessary to defend against modern attacks. When BrickStor SP detects irregular or malicious behavior, it can alert your organization’s security or infrastructure team and stop the user and host from being able to steal, manipulate and access files until the behavior is investigated and mitigated.
BrickStor SP uniquely combines active security capabilities with high performance data storage to create an enterprise class zero trust solution for file storage. It’s a drop-in replacement for your existing NAS, can run as a virtual machine at the edge or in the cloud, or can easily leverage existing storage capacity already within your infrastructure. You already know your data is important. It’s time to start protecting it like it is.
Contact
Phone: +1 443-276-6973
Email: RackTop info
Support: Customer log-in
Address: 8170 Maple Lawn Blvd. Ste. 180
Fulton, MD 20759 USA
Request more information