BrickStor SP for RMF Compliance
Compliance requires implementation of controls, continuous monitoring, and enforcement, as well as evidence of controls and enforcement.
Our platform provides paramount security, automates continuous monitoring, and streamlines evidence collection, enabling organizations to meet RMF requirements set forth by frameworks such as NIST 800-37, 53, and 137.
Industry Applications

Government
RackTop’s solutions are accredited for federal deployment and actively align with the JSIG/RMF and supporting secure operations for classified and unclassified government data.

Healthcare
With healthcare providers facing rising cyberattacks, RackTop enables RMF-aligned protection for electronic health records (EHR), PACS, and clinical data. It integrates access control, encryption, and audit-ready compliance for HIPAA and other standards.

Commercial and Other Regulated Industries
Financial, energy, and insurance organizations leverage BrickStor SP to safeguard sensitive information, comply with RMF controls, and simplify regulatory audits.
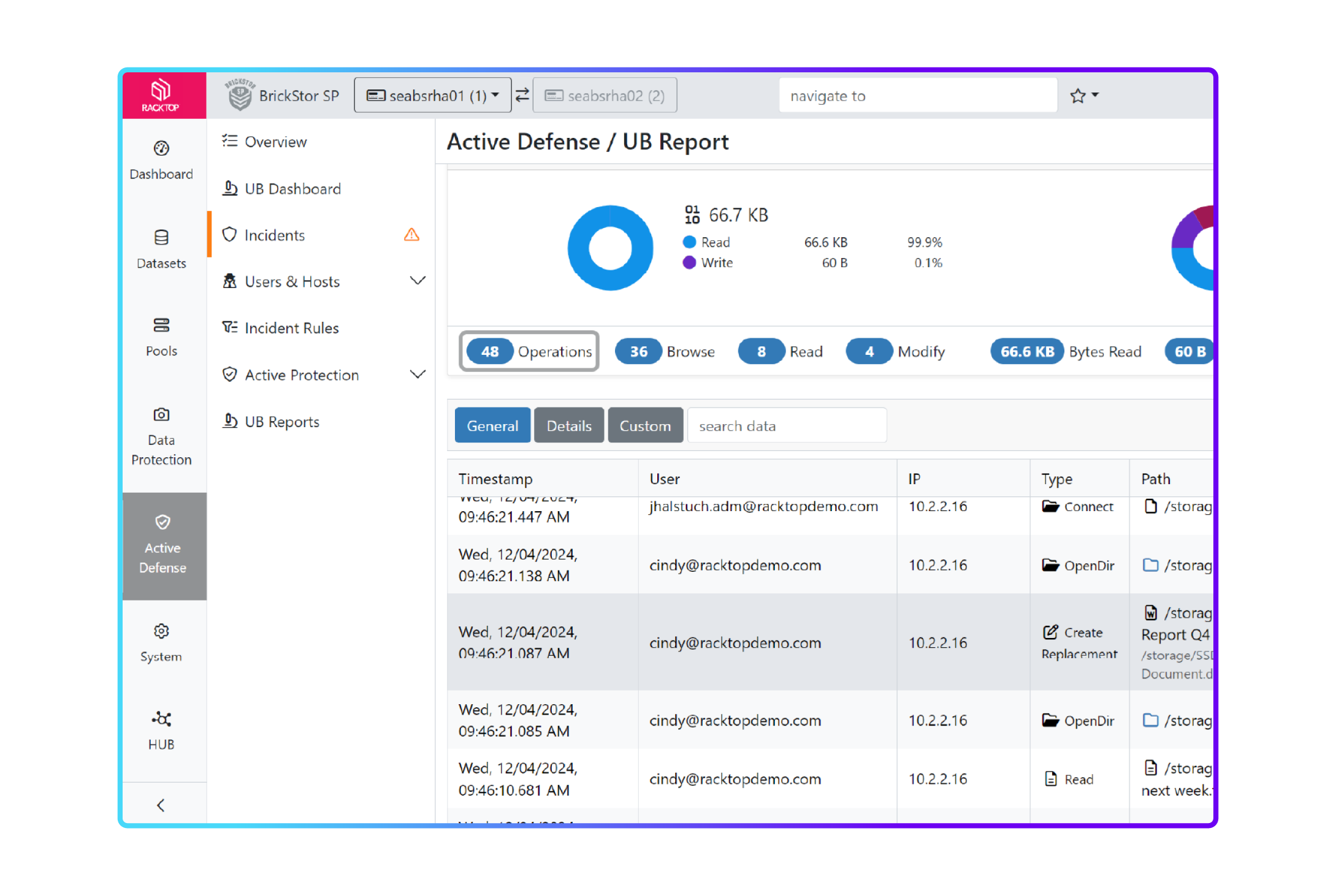
BrickStor SP Maps to All Revelant Areas of RMF
Integrated compliance reports demonstrate ongoing evidence of controls and compliance
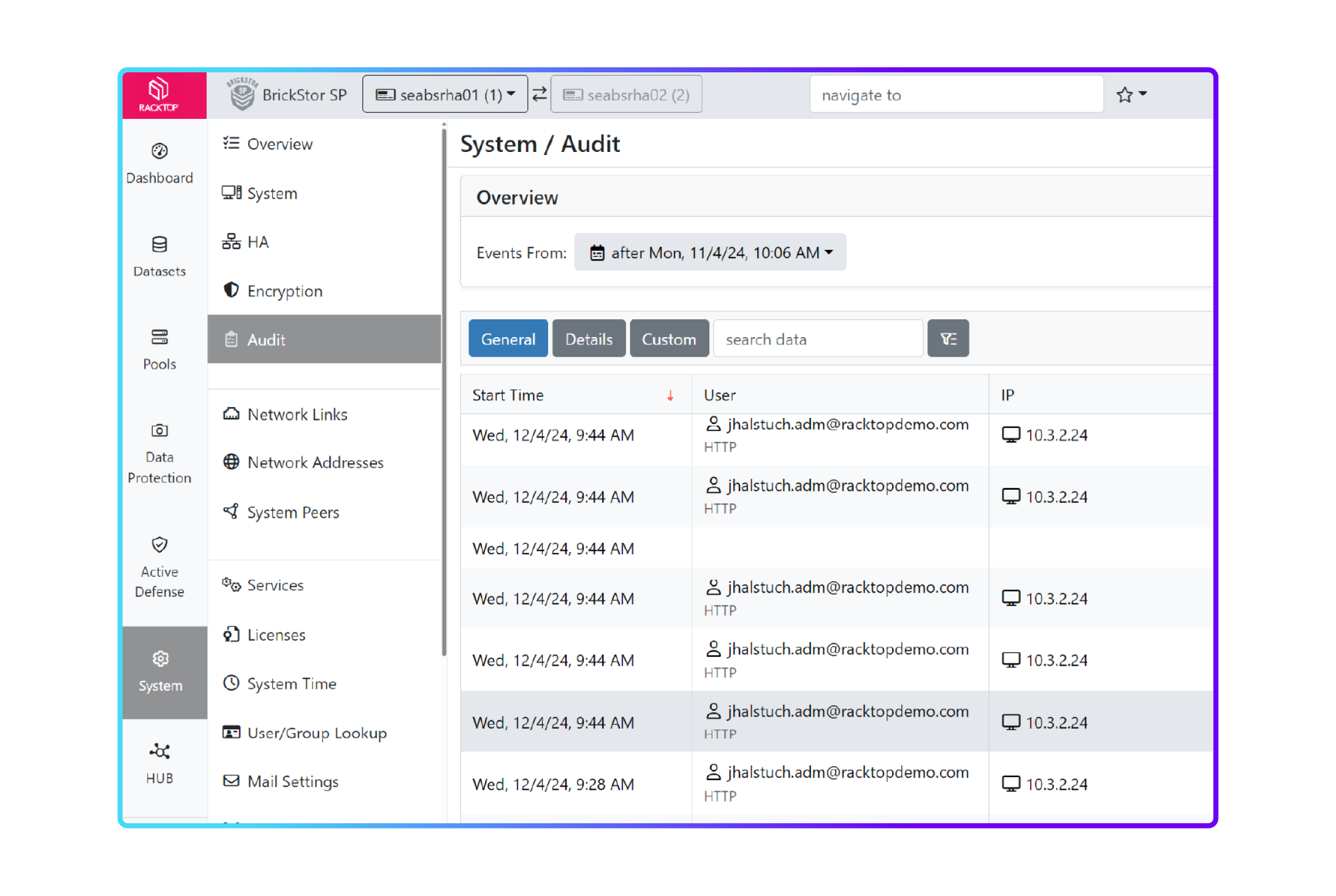
Audit Report